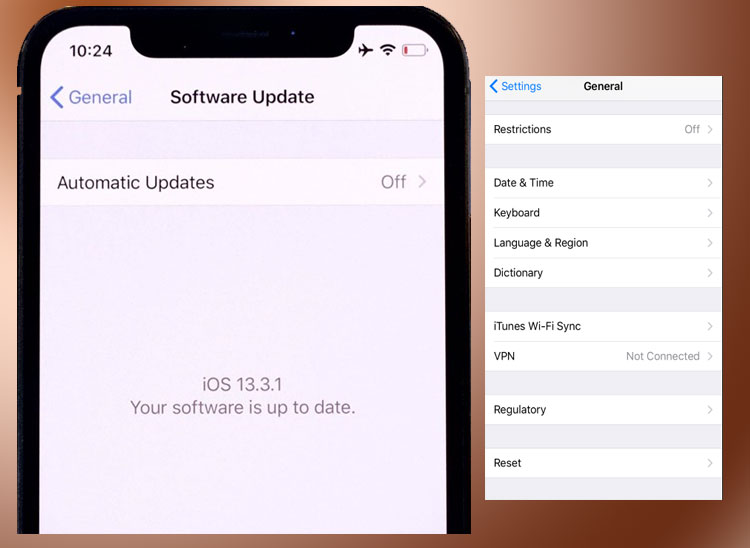
The latest update of iOS 13.3.1 come with a security Vulnerability that prevents VPN from encrypting the user data. This may lead to exposing the user’s personal and location data. This security vulnerability is discovered by a user of ProtonVPN. The researchers at Proton Technologies AG detailed vulnerability with the iOS 13.3.1 and explained that the iOS is not closing existing connections.
The latest version of Apple iOS 13.3.1 comes with an unpatched bug which stops the VPN from encrypting all the internet traffic which passes through the VPN. This bug restricts the iOS 13.3.1 from closing all existing Internet connections, which may lead to exposure of user personal data and location.
As per the reports this bug is still not fixed in latest iOS 13.4 updates, so the users of iOS 13.4 will face the same issue even after updating their Apple devices. This bug could lead to the exposure of user’s personal data or provide their IP address to the attackers by bypassing the default VPN encryption. There is no official word on the fixing of this bug, but due to severity of bug Apple might release the update incoming days/weeks.
The Virtual Private Network or VPN is a special software and server that is used to provide the secure connection between client and server. If VPN is enabled on the user’s device, then it usually closes all the Internet connection and all data pass through the VPN tunnel. The VPN is used in corporate and secured environments for communication. The VPN on iOS device provide the same functionality, but due to a bug in the iOS 13.3.1 the user’s private data might get exposed.
In real environment most of the internet connection used for connecting to the server is short-lived and in most cases it is re-established through the VPN tune of the iOS device, but there are few which lives for a longer period of time. The Apple’s push notification server work with the long lived connection and the connection lives for longer hours outside the tunnel. The long established connection might create security issues and this is one of the major security concerns.
“The VPN bypass vulnerability could result in users' data being exposed if the affected connections are not encrypted themselves (though this would be unusual nowadays). The more common problem is IP leaks. An attacker could see the users' IP address and the IP address of the servers they're connecting to,” the ProtonVPN explained the bug in a post.
As per reports there is no workaround for this bug, so the VPN service provider is also not able to provide any solution to this issue. There is no fix for this because the bug is at the operating system level. The users of iOS 13.3.1 and iOS 13.4 can mitigate the VPN bypass vulnerability by turning off and then switching on their phone frequently. Users can also achieve this by switching on the airplane mode and then switching off the airplane mode. This is a serious bug with the iOS 13.3.1 and iOS 13.4, Apple is expected to release a fix for this bug in coming days.